“Can I hack a cell phone through its number alone? If so, how can I do it with ease with no knowledge of programming or hacking?”
I often get these queries from a lot of people, including concerned parents, suspicious spouses, vigilant employers, and curious geeks (like me).
People want to find out how to hack a phone when all they have is a phone number. This basically means that the person would not be able to touch the cell phone in order to hack it.
If you want to find out the answer to this question, the things that I am going to tell you here might interest you a lot:
Part 1: Can a Phone Be Hacked with Just the Number?
In one simple word- YES. It is actually very easy to hack a cell phone, even if all you have is the phone number.
In fact, there are various ways to hack a cell phone through its number. The choice is entirely upon the user, based on their knowledge of programming and the resources they have to dispense.
You can even hack a cell phone without ANY knowledge of programming or any other thing required. This can be done remotely, from any corner of the world.
Without taking too much of your time, let me talk about 4 ways to hack a phone with the number.
Part 2: How to Hack Someone’s Phone via Spyic
If you are looking for a trusted, reputed, secure, and reliable phone-monitoring app, try Spyic. You will be completely bowled over with its user-friendly and intuitive interface. Not to mention its rich features to monitor the target remotely!


This app is used globally across 190 countries by millions of users. That is why top media houses have been featuring it regularly on their platforms. As mentioned earlier, if the target is Android, you will need to first install the spy app.
Spyic features a very lightweight Android app for this purpose. The app only takes less than 2M of space. Want to remove the app after installation? No worries. You can remotely uninstall the app in one click. What’s more, the app does not drain the battery and runs secretly.
The Spyic iOS solution is even more special. It’s the perfect solution for those wanting to know how to hack a mobile phone with just the number. The solution is cloud-based. There is no need to install any app on the target phone. You can use any browser to access all data.
2.1 Why Should You Use Spyic?
Do you want to know more about the unique features of Spyic app? Let us see them all one by one.
- SMS Tracking: After you begin monitoring the phone by using the Spyic app, all received and sent messages can be seen. You can track media files easily and remotely.
- Track Location: This app helps one to locate the GPS data of the target phone in no time. You can monitor at what time the target is available at a particular location with the timestamps. You will get alerts when the target phone moves across geo-fencing boundaries.
- Social media monitoring: If you wish to monitor social media activities you have no better solution then Spyic. You can easily access Snapchat, Facebook Messages, Instagram messages, and WhatsApp. You can also see the media files exchanged.
- Call Tracker: You can remotely monitor all calls including the ones incoming and outgoing. Callers’ details and call duration are also accessible using this app.
2.2 Hacking All Email and Social Media Accounts With Android Keylogger
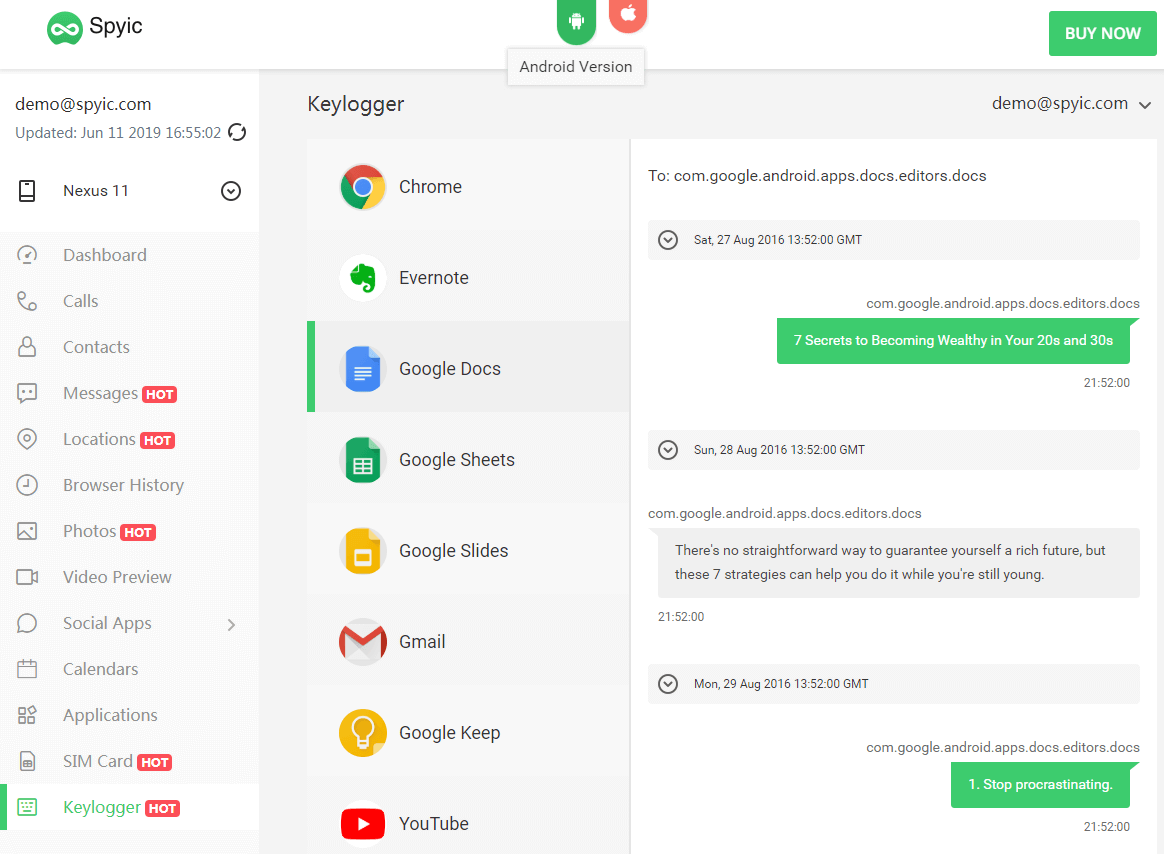
If you wish to go a step further with the Spyic app on an Android device, you can use the keylogger feature. By using this feature, you can track all key presses on the target phone.
The keylogger logs everything typed on the phone by the target.
The keylogger saves the usernames and passwords of all of the accounts visited by the user. Thus, you will be able to hack into all email and social media accounts. This makes the keylogger a very powerful feature indeed.

2.3 How to Hack a Mobile Phone: Step-by-Step Tutorial
Did you know that rooting and jailbreaking are not needed to hack social media accounts? Spyic is unique in this way. Most spy apps require you to perform the rooting/jailbreaking operation first for advanced tracking. However, Spyic simplifies the process greatly.
The installation process of Spyic app is very simple and takes under 5 minutes. Spyic app is available for both Android and iOS phones.
Step-1: The very first step is to make a free account on the official Spyic website. You will find it is very simple and user-friendly and takes a few minutes only.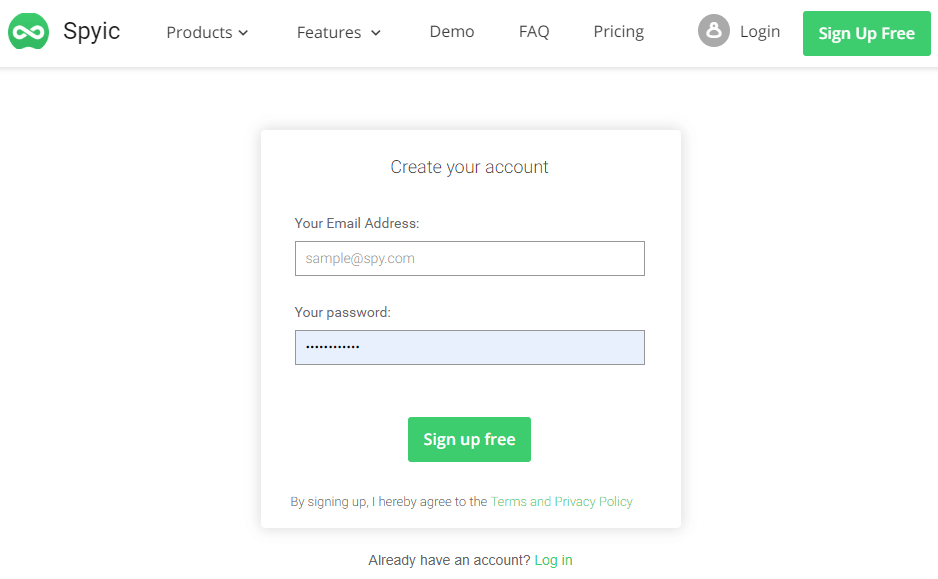

Step-2: Now select your phone type. The Spyic’s Android solution requires installation on the device. Allow all permissions which the app asks.

To hack an iPhone with just its number, you can use the Spyic iOS solution. There is no installation needed. You will just need the iCloud credentials of the target. You can use any browser as per your liking to monitor the data remotely. This way, it can’t be detected!
Just verify the iCloud credentials of the target phone. Allow the app to sync all data for a while.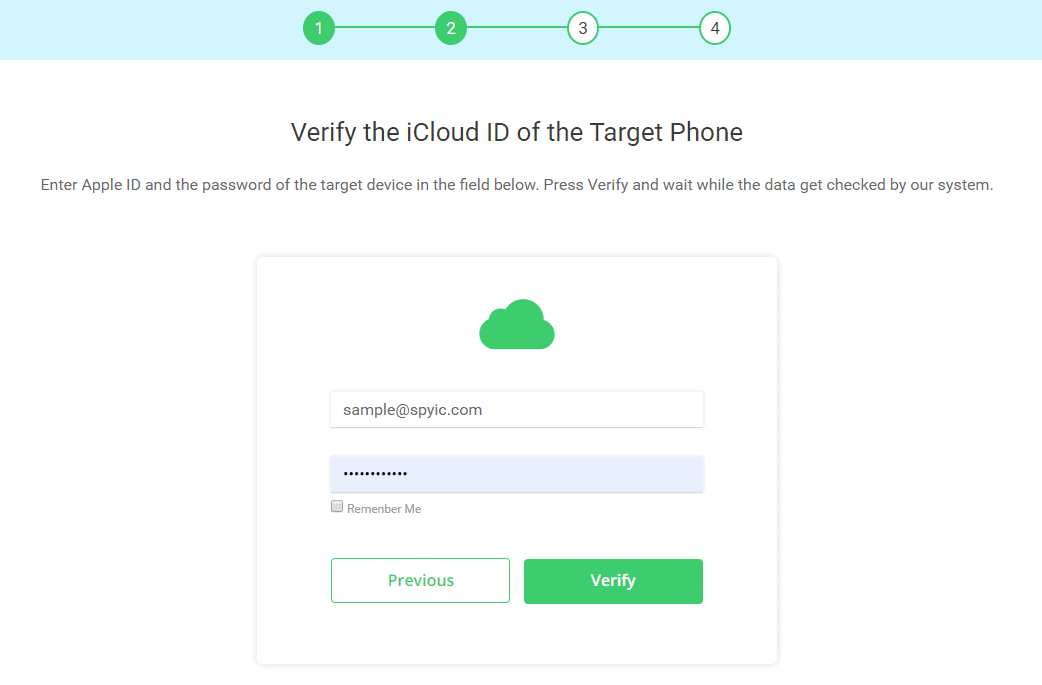

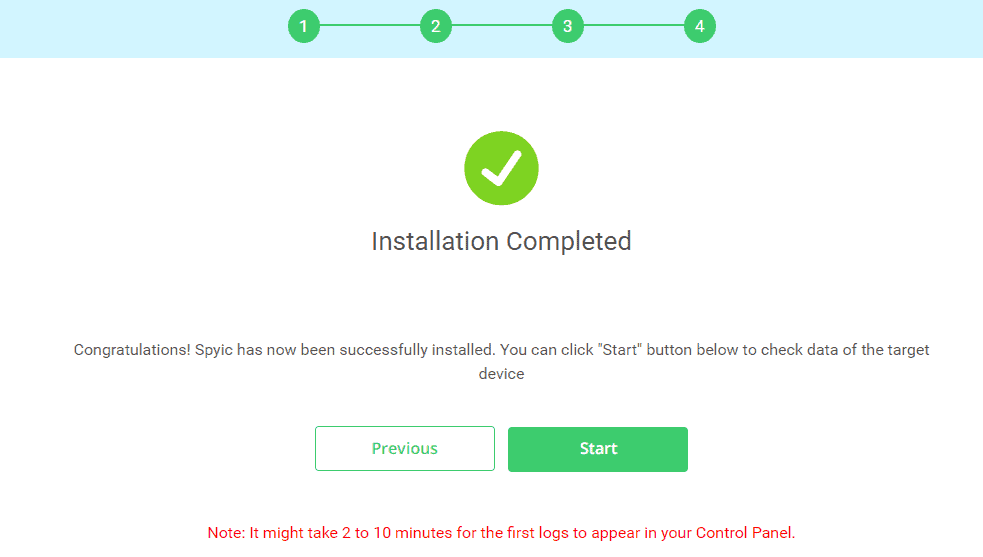
Step-3: After successfully verifying the account, you have set up almost everything. You can start the monitoring activity of the target phone.
You may now select to see the WhatsApp, SMS, Facebook Messages, and Instagram messages. There are also several other functions on your control panel dashboard to choose from.
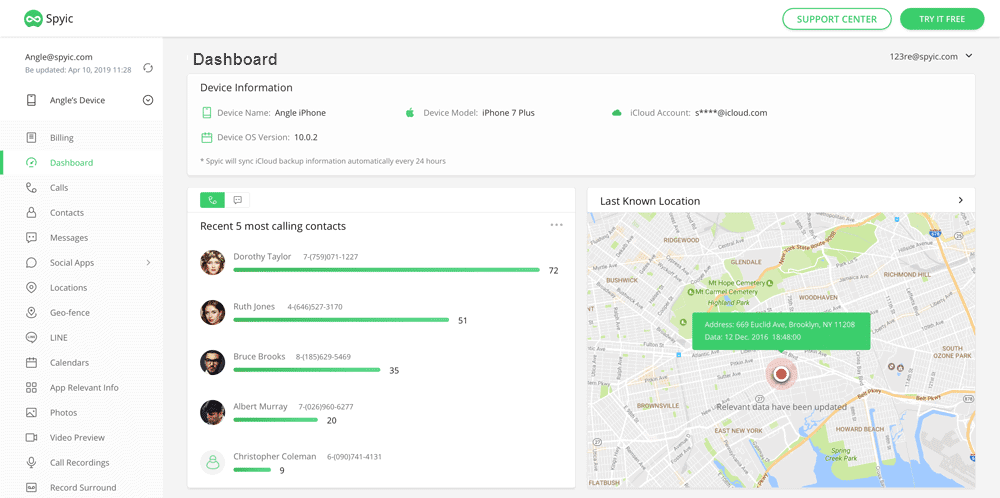



You can choose whatever you wish to hack and access it remotely. As you have observed, the installation process comprises of just three easy steps. We highly recommend that you check out the Spyic live demo on this link. This is a great way to see how it works closely.
2.4 Stealth Technology to Secretly Monitor Data
By using advanced stealth technology, the Spyic app remains hidden on Android phones. The icon of the app is deleted just after the installation process. The app works in the background. Hence the most amazing feature of the Spyic app is its secret and discreet working.
This is a very important thing to ensure, indeed. If a spy app draws attention to itself, the target user will know he/she is being monitored. Spyic takes care of this part too.
Part 3: Hire a Hacker to Hack a Cell Phone Remotely


Nowadays, the internet is flooded with so many hackers claiming to accomplish phone hacking and whatnot. While you may not find many genuine hackers on the regular internet, an hour or two on the dark web might get you a genuine one.
However, the cost of hiring a hacker can run very high, even in thousands of dollars. There might be some hackers willing to work for cheaper, but you never know if they are genuine or not.
There is a good chance that you hire someone, pay them, and end up losing your money. Mind you, the world is full of scams and frauds. Moreover, it is possible that the hacker you hire might use the same trick mentioned in Part 1, or the other parts of this article.
I have even heard stories of people hiring hackers and the hackers then blackmail the people after getting the hacked data. Therefore, if you go ahead with this method, take extra caution on every step.
Part 4: Using WiFi Sniffer to Hack a Cell Phone
WiFi sniffers are ethical hacking tools that hackers use to assess network vulnerabilities. However, if you have a good technical handle on things, you can use a WiFi sniffer tool to hack a cell phone remotely. There are various WiFi sniffing applications available on the internet.
A WiFi sniffer (also called a wireless packet sniffer) analyzes all the incoming and outgoing data of the phone. This can give you some useful information about what they are doing on the internet (like their internet activity).
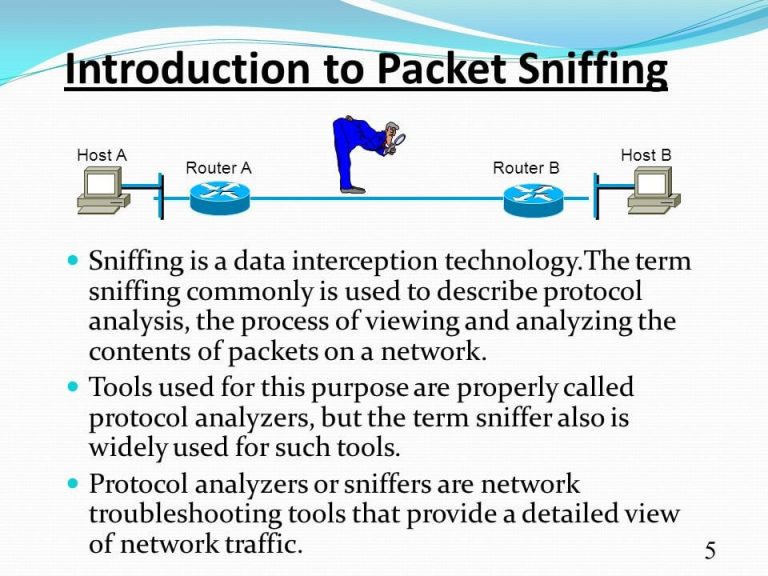

However, this information will be present with a lot of other useless things, so you need to know how to filter out this information.
Also, it will not show you in-depth data such as their private messages, which apps like Spyier can accomplish.
Part 5: SS7 Vulnerabilities Exploit for Cell Phone Hacking
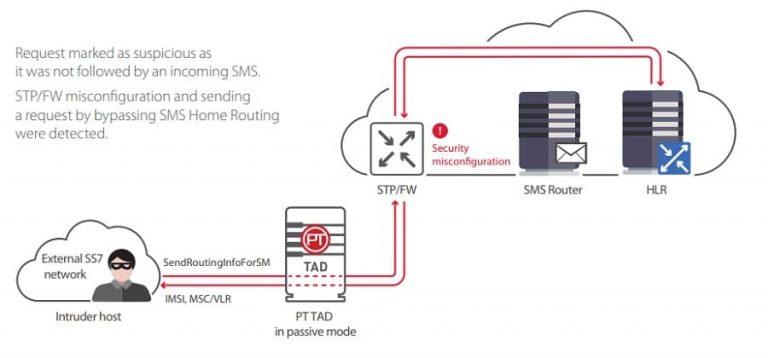

This method is a step up the technical ladder, for people who are very knowledgeable about programming and ethical hacking tools.
SS7 is a protocol that bridges the gap between two phone networks. It stands for Signalling System No. 7 and is generally implemented by your phone carrier.
As your phone carrier handles your phones and SMS messages, all this data is transferred over the SS7. You can exploit the vulnerabilities present in the SS7 protocol to extract any call or message data of the user.
However, SS7 is generally updated and monitored by security services. Therefore, you need a very high level of technical expertise to exploit these systems. Also, if you succeed, you will only get their call and message data.
Part 6: Comparison of Various Phone Hacking Methods
Here is a table that compares all the phone hacking methods we discussed above:
1. Spyic solution:
- Cost: $9.99 per month
- Difficulty: Very Easy
- Secrecy: Very High
- Risk: None
- Data Discovery: All phone data
- Technical Knowledge Needed: None
2. Hire a hacker solution:
- Cost: $1000 and above
- Difficulty: Low
- Secrecy: Low
- Risk: High
- Data Discovery: All phone data
- Technical Knowledge Needed: None
3. WiFi Sniffer solution:
- Cost: Based on the application you use
- Difficulty: Medium
- Secrecy: Very High
- Risk: None
- Data Discovery: Internet activity
- Technical Knowledge Needed: High
4. SS7 Exploits solution:
- Cost: Variable
- Difficulty: Very High
- Secrecy: Very High
- Risk: High
- Data Discovery: Calls and SMS
- Technical Knowledge Needed: Very High
Endnotes
After the comparison table above, you can immediately decide which category you fall into and which method you want to go ahead with. On one hand, we have Spyic, an app perfect for people looking for an easy hacking solution that does everything for them.
On the other hand, there are methods like SS7 exploits, which work well if you are a tech pro with years of experience in the field.
All in all, if you don’t really know what you are doing, don’t take a risky approach as it might end you in trouble.
Be safe!
This post is also available in: Deutsch (German)







